Softline Holding plc began trading under the brand name Noventiq after divesting part of its business in October 2022.

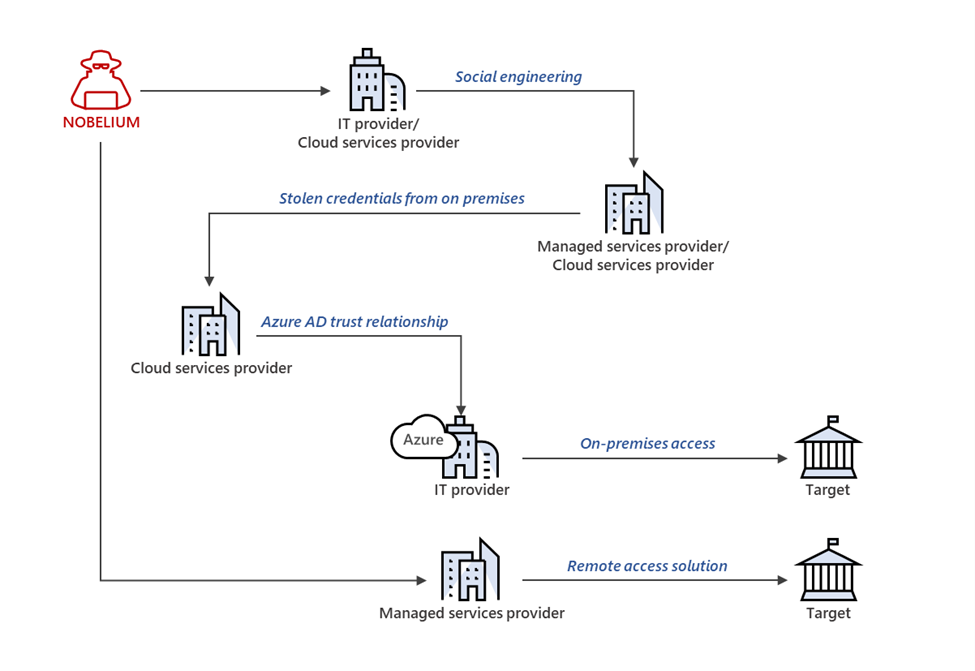
The Microsoft Threat Intelligence Center (MSTIC) has detected nation-state activity associated with the threat actor tracked as NOBELIUM, attempting to gain access to downstream customers of multiple cloud service providers (CSP), managed service providers (MSP), other IT services organizations (referred to as “service providers” for the rest of this blog) that have been granted administrative or privileged access by other organizations, and downstream customers of service providers and other organizations are also being targeted by NOBELIUM in this supply chain attacks.
How does NOBELIUM work?
Microsoft has observed NOBELIUM targeting privileged accounts of service providers to move laterally in cloud environments, leveraging the trusted relationships to gain access to downstream customers and enable further attacks or access targeted systems.
Are these attacks originated from product security vulnerability?
These attacks are not the result of a product security vulnerability but rather a continuation of NOBELIUM’s use of a diverse and dynamic toolkit that includes sophisticated malware, password sprays, supply chain attacks, token theft, API abuse, and spear phishing to compromise user accounts and leverage the access of those accounts. These attacks have highlighted the need for administrators to adopt strict account security practices and take additional measures to secure their environments.
What is responsibility of CSP, MSP?
Softline, as a Microsoft worldwide cloud service provider (CSP), works closely with MSTIC and a team of security specialists to observe and monitor threats to prevent them from spreading. Simultaneously, we have also engaged directly with affected customers to assist with incident response and drive better detection and guidance around this activity.
Here are 3 steps so that you – downstream customers can take to reduce the potential impact of this NOBELIUM activity!
1. Review, audit, and minimize access privileges and delegated permissions
Review, harden, and monitor all tenant administrator accounts:
All organizations should thoroughly review all tenant admin users, including those associated with Administer On Behalf Of (AOBO) in Azure subscriptions and verify the authenticity of the users and activity. We strongly encourage the use of strong authentication for all tenant administrators, review of devices registered for use with MFA, and minimize the use of standing high-privilege access. Continue to reinspect all active tenant admin users accounts and check audit logs on a regular basis to verify that high-privilege user access is not granted or delegated to admin users who do not require these to do their job.
Review service provider permissions access from B2B and local accounts:
In addition to using the delegated administrative privilege capabilities, some cloud service providers use business-to-business (B2B) accounts or local administrator accounts in customer tenants. We recommend that you identify whether your cloud service providers use these, and if so, ensure those accounts are well-governed, and have least-privilege access in your tenant. Microsoft recommends against the use of “shared” administrator accounts. Review the detailed guidance on how to review permissions for B2B accounts.
2. Verify multi-factor authentication (MFA) is enabled and enforce conditional access policies
MFA is the best baseline security hygiene method to protect against threats. Follow the detailed guidance on setting up multifactor authentication in Microsoft 365, as well as the guidance on deploying and configuring conditional access policies in Azure Active Directory (Azure AD).
3. Review and audit logs and configurations
Review and audit Azure AD sign-ins and configuration changes:
Authentications of this nature are audited and available to customers through the Azure AD sign in logs, Azure AD audit logs, and the Microsoft 365 compliance center (formerly in the Exchange Admin Center). We recently added the capability to see sign-ins by partners who have delegated admin permissions. You can see a filtered view of these sign-ins by navigating to the sign-in logs in the Azure AD admin portal, and adding a filter ‘Cross-tenant access type: Service provider’ on the ‘User-sign ins (non-interactive)’ tab.
Review Existing Log Availability and Retention Strategies:
Investigating activities conducted by malicious actors places a large emphasis on having adequate log retention procedures for cloud-based resources including Office 365. Various subscription levels have individualized log availability and retention policies which are important to understand prior to forming an incident response procedure.
Read more: Click here
Contact Softline to get in-depth consulting!
